To understand what a specific software does you can take a look at...
Vulncode-DB – A vulnerable code database
To understand what a specific software does you can take a look at...

With the staggering amount of features that were introduced through...
Hey PHP, those variables look like garbage don’t you agree? No...

It all started by auditing Pornhub, then PHP and ended in breaking...

To understand what a specific software does you can take a look at its source code if available. However, if you want to find more than just a high-level description for...
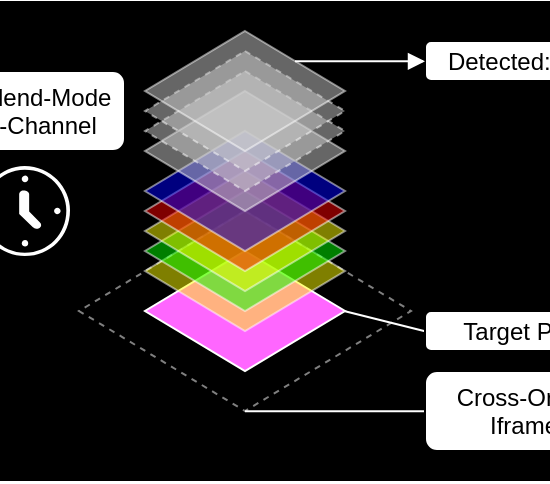
With the staggering amount of features that were introduced through HTML5 and CSS3 the attack surface of browsers grew accordingly. Consequently, it is no surprise that...
Hey PHP, those variables look like garbage don’t you agree? No? Well look again… tl;dr: We have found two use-after-free vulnerabilities in PHP’s...
It all started by auditing Pornhub, then PHP and ended in breaking both… tl;dr: We have gained remote code execution on pornhub.com and have earned a $20,000 bug...
While auditing Pornhub we have stumbled across several pages where user input was evaluated by unserialize and the result was reflected back to the page. After...
If you want to use Linux as your main operating system and don’t want to do compromises like using a dual-boot solution with Windows there is an alternative called...
Hey folks, today I write about a (probably unknown) TeamSpeak 2 session hijacking vulnerability. TeamSpeak 2 is a voice-over-Internet Protocol (VoIP) software that was...